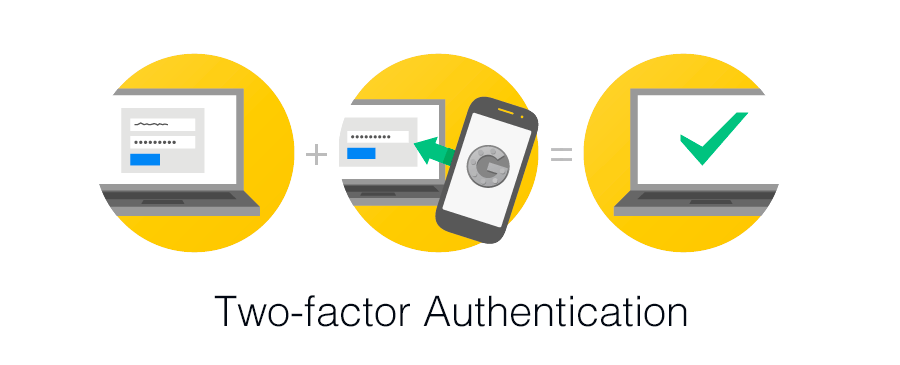
How to secure Vtiger CRM, protect valuable data from potentially being taken by employees when they leave or hackers. It is a very critical issue, and the solution is not as easy as you might think. That's why we would like to share some interesting tips. User login into the CRM, It will be prompted for the username and password as usual. If the password is correct, instead of the dashboard, he/she will see another screen when the user will need to enter a code generated with google auth app. two-factor authentication This type of authentication provides an additional layer of security as an attacker is unlikely to able to crack both layers to get a bypass. How to secure your VTiger CRM Data? This is how adding Vtiger Two Factor Authentication, protects your data. Brute force attack is mostly all hackers use to force their way into your site is using a brute force attack. This way, repeatedly trying to guess your username and password, often the password is not strong enough it can be guessed easily after some attack. When the hacker has full access to your dashboard panel, then he can do anything. So this the reason you should make sure your password is powerful. So here is one suggestions combinations: uppercase and lowercase, special characters and numbers. This one is a great suggestion for change a password in once in a month. Easily configure password policies within a few seconds admin can easily configure your Vtiger CRM login page. VGS Secure Passwords Module Features Vtiger CRM administrators can configure as per below strategies: How does Vtiger Password Policy work? After installing the module Click on > Settings > Other Settings > VGS Secure Passwords, click there, and you will be able to set the password pattern to install as policy. Yes, in cloud hosting make a real impact on your business, deploying your CRM in the cloud can be a big revolution or a simple way to optimize your IT It’s all depending on the unique need of your company. In Primary factor, it’s very important to secure website data structure their need for data access, the resources you have available. The good things about Cloud Hosting are several: In the following paragraph, you will be able to read three rules that make it exponentially harder to crack your password. The strategies employed by password crackers so you need to know about the unbreakable password method. After you have created your secure password, it’s not fully secure so one thing remembers: never reuse the same password again. There are some many different approaches you can take to create strong passwords, so you never have to again use: Make sure that all the systems of your employees are installed with antivirus and check that it is regularly updated with prevents malware incidents and protects data in the layer. So antivirus scan data often it can determine the vulnerability of CRM under protection data. In Dynamics CRM Online to users with trusted IP addresses to reduce unauthorized access. When trusted IP address restrictions are applied to a user profile and the user attempt to log in from an unauthorized IP address, So CRM access is blocked. The last one on this post, we have been focusing on stolen data, but data protection also includes defending against lost data this is more important. The CRM system in the cloud is not an excuse for skipping backup data. But Make sure this is well performed and regularly and keep a copy of CRM data by the cloud service provider. Do you want to start a fully secured Vtiger CRM project? Have anything interesting in your mind? Get in touch with us! or direct send email info@iihglobal.com.1. Vtiger Two Factor Login Authentication
2. Brute Force Password Hacking Attacks
3. Professional Hosting
4. Unbreakable password
5. Install and update antivirus protection up to date:
6. Managing trusted IP addresses